SI-CERT, the national CSIRT of Slovenia has been handling reports of ransomware attacks on a regular basis since April 2012. Until 2019, attack victims were selected randomly as part of a mass-volume campaign aiming to spread the virus. However, since 2019 the attacks have been more targeted. In most cases, the vector of infection is either a malicious email that contains a malicious attachment or link, or an attack via an inadequately secured Remote Desktop Protocol. Nonetheless, cyber criminals can also exploit new vulnerabilities to gain unauthorised access to target networks.
The Course of The Attack
In a targeted attack, cyber attackers first select targets that they perceive as having the ability to pay a higher ransom. If the infection happens via email (usually with a custom-built Trojan) or they find a publicly available service that allows access to the enterprise’s network, they install a Remote Administration Toolkit (RAT) on the compromised system. They then use it to monitor the structure of the network and, using various intrusion tools, obtain authentication data and access to other systems in the network. In the Windows environment, their main target is the domain controller.
By analysing the obtained information, they assess the value of the data and on that basis determine the ransom amount, which can in some cases exceed €100,000. If the system search provides them with databases that have a high business value for the enterprise, or contain personal data, they steal it.
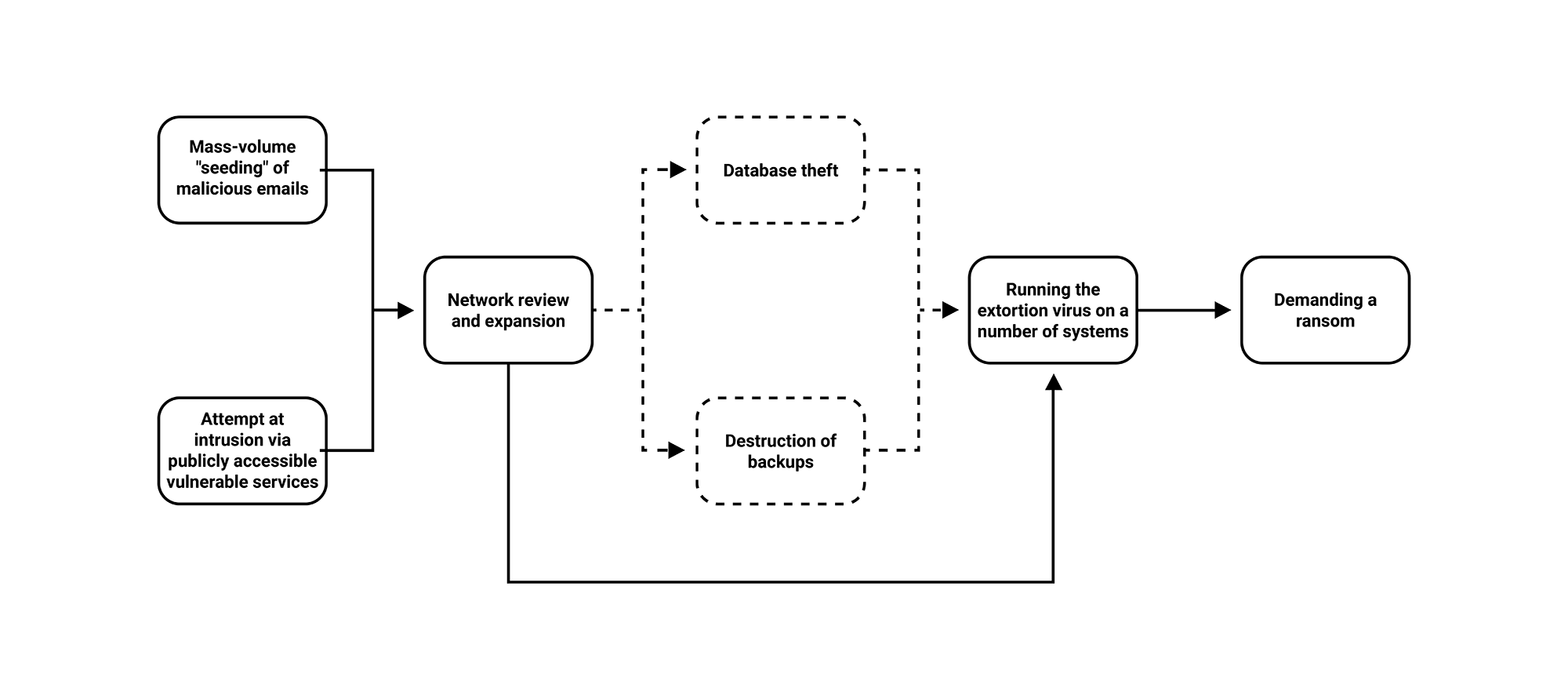
Furthermore, they try to find backup copies of the system and (if possible) arrange for its destruction. In the last step, they download and run the ransomware on as many systems as possible. The virus encrypts the data and consequently paralyses or impedes the enterprise’s operation. Perpetrators demand a ransom to decrypt the data and may threaten to publish sensitive data if any were found.
Ransomware Attack Vectors
1. Intrusion via an inadequately secured Remote Desktop Protocol or other vulnerability
In a business environment, Remote Desktop services are most commonly used to access server infrastructure. Insufficient or inadequate remote desktop protocol protection enables cyber criminals to access and install malware.
The most common reason for a successful intrusion is the use of weak passwords, which can be identified by brute force and dictionary attack, or the use of the same passwords for different services (password recycling). Misused authentication data are also traded in illegal markets that are usually located on the dark web. A large number of the cases examined showed that attackers carried out activities on weekends when they were less likely to be detected.
In the event of a delayed or improper installation of patches, the vulnerability of the service may further facilitate unauthorised access to the infrastructure by cyber criminals. Examples include the BlueKeep vulnerability in Windows RDP, and the CVE-2020-0688 vulnerability in the Microsoft Exchange server. Both vulnerabilities allow perpetrators to run any code remotely (RCE, Remote Code Execution).
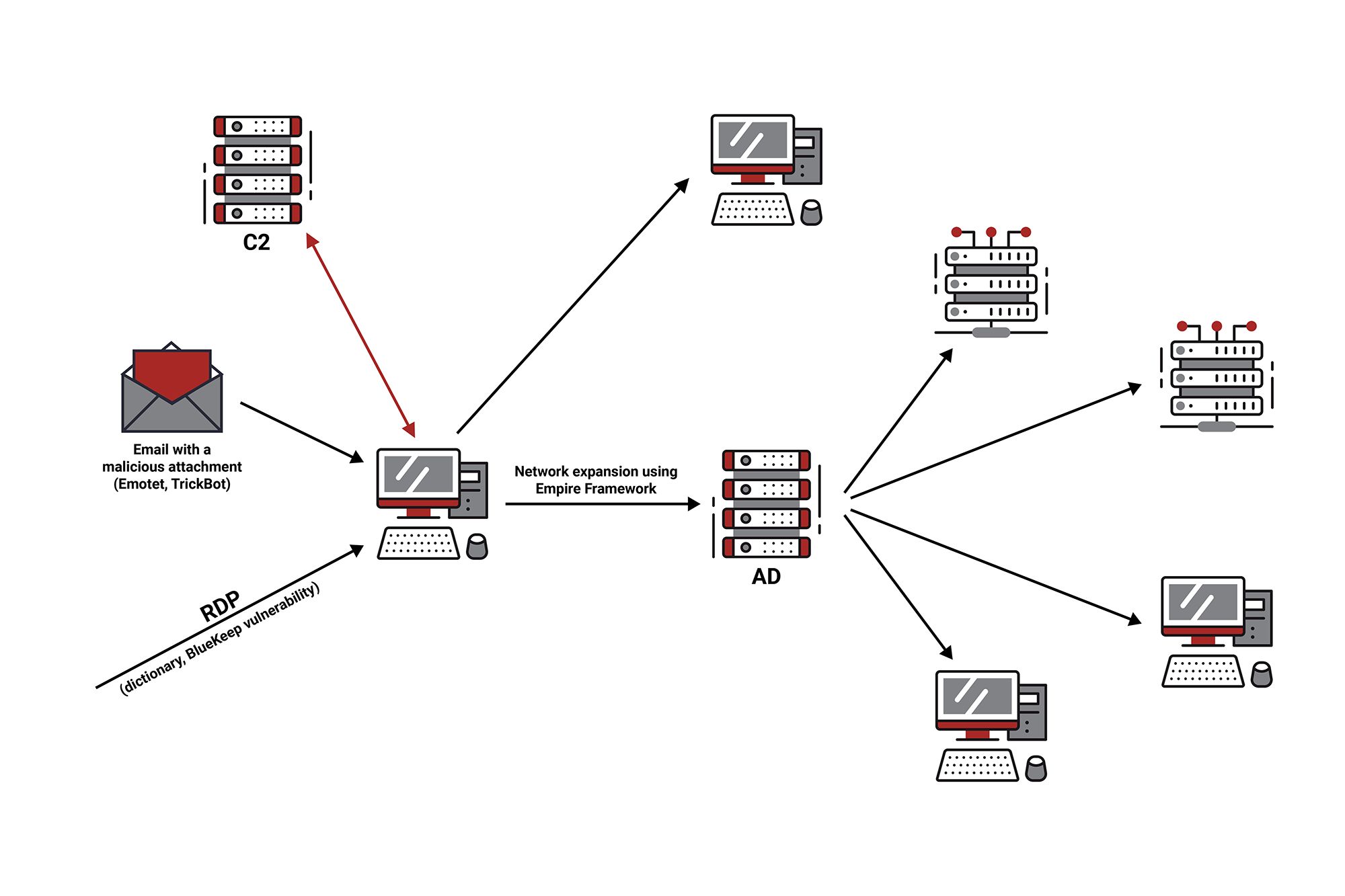
2. Attacks via email
Infections with a Trojan virus such as the Information Stealer and Remote Access Trojan (RAT) can also lead to infections with ransomware.
These are most often spread via email. The content of the message tries to persuade the recipient to open the attachment or click on the link to download the malware to their system. In some cases, the infection can originate from the infected computer of a business partner as a response to past correspondence.

- The Information Stealing Trojan retrieves stored passwords from installed web browsers, email clients, FTP clients, etc. Some of them also install a keylogger on the system, which records entries on the keyboard (e.g. entered passwords), but they can also contain a component for downloading files from the web (downloader). Based on this functionality, cyber attackers can transmit and run the ransomware on a compromised system.
- The Remote Access Trojan creates a backdoor for remote access to the victim’s computer, allowing the attacker to access the compromised system. After scanning the entire network, checking for access options to all available servers, computers, and network and external media, the perpetrators install and run the extortion virus.
3. Other Ransomware Distribution Methods
In more advanced attacks, where cyber criminals target a specific target, the initial intrusions into the system may also be the result of other hacking techniques, such as:
- Drive-by Download, which occurs when the victim visits (“drives by”) and opens a web page in the browser to which the attacker has previously installed an additional malicious code. This infects the victim’s computer through a vulnerability in a browser or other software.
- Watering Hole Attack, which is a version of a drive-by download attack intended for a specific user profile. Attackers choose a site (such as a military equipment manufacturer or provider of hardware and software solutions for energy systems) that these users are known to visit on a regular basis. By compromising the chosen site, the Trojan may infect its visitors.
- Infected USB sticks and other peripherals.
- Intrusion via an inadequately protected WiFi network.
- Physical access to one of the systems on the network.
Best Practices to Keep Your Data Secure
Cyber security defence against ransomware includes technical measures such as the use of an anti-virus, firewall, filters on servers, VPN connections, intrusion control and prevention systems, as well as regular education of users or employees. However, 100% protection can never be assumed in the information security domain, so the best protection against ransomware is a proper backup, i.e. a copy of critical data and resources stored off-network on a separate device or devices, and regular scans of backups for infection and run data recovery drills.
To protect the local network, we recommend the introduction of Network Intrusion Detection Systems (NIDS) and Host Intrusion Detection Systems. The implementation of the SIEM (Security Information and Event Management) system enables the tracking of activities and analysis of log records and events on the network. The design of the network should preferably be divided into areas (publicly accessible servers, internal network) with restrictions on the data exchange between them.
We also recommend developing a strategic action plan in the event of an attack on the enterprise’s information infrastructure (Disaster Recovery Plan). This should include a set of procedures and tasks for the groups, individuals, and external contractors involved in resolving the situation. At the same time, it is of utmost importance to create a scenario to check and add action steps/update action plans.
In addition to all of the above, it is also necessary to closely define the policy of connecting users’ own devices and the use of employees’ external media (e.g. USB sticks) in the enterprise’s or organisation’s Information System.
About SI-CERT

Read more on the GÉANT Cyber Security Month 2020: https://connect.geant.org/csm2020







