Social engineering is the act of manipulating or tricking people into certain actions, such as giving out personal or financial information that can be used to commit fraud. It’s an act, but also an art; social engineers are very good at influencing victims through their emotions, for example by pretending to be someone in need of help. They may also pretend to be an authority figure. Or evoke curiosity through news on current events. Or offer a discount with limited availability. Their tricks are endless.
By Laura Pooley, information security officer at JISC
Click on the links below to jump down to the different sections or simply scroll through and take it all in:
Vishing
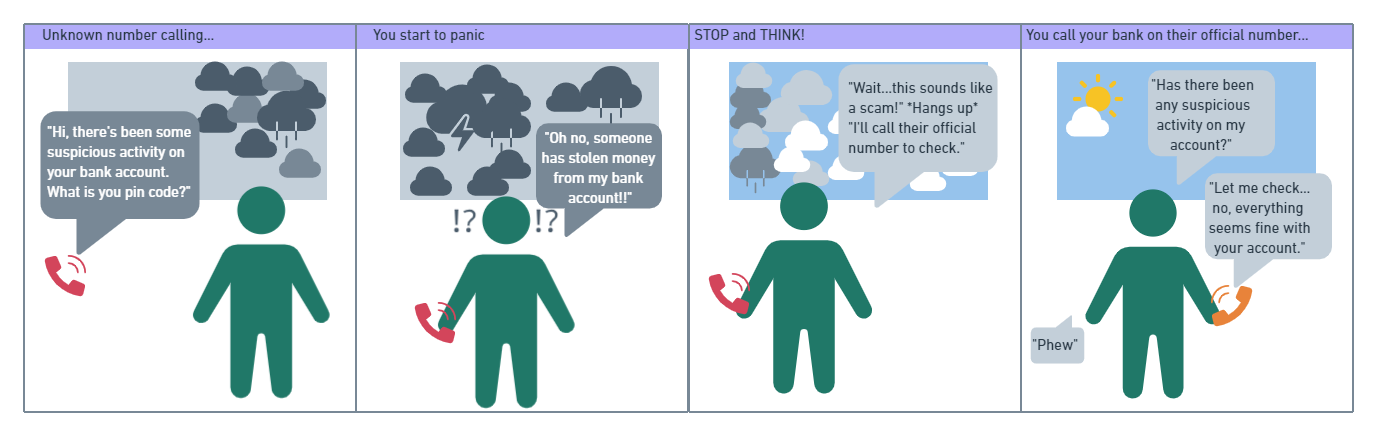
We’ve probably all received a phone call like this:

If you think it sounds like a scam, it probably is, so put the phone down, block the number and report it to your local fraud prevention authority.
Less savvy people may give out personal data, banking information or access to their computer – and before they know what’s happened, the criminals are going through files and personal information in the background. The data gathered here could allow fraudsters to take out credit in your name. You might be looking at serious debt. Or identity theft.
It’s easy to panic when you receive a phone call like this and that’s the point – the criminal wants you to feel under pressure and scared of the consequences if you don’t comply, so you don’t stop to think and question.
Smishing
How would you feel if you received one of these text messages?
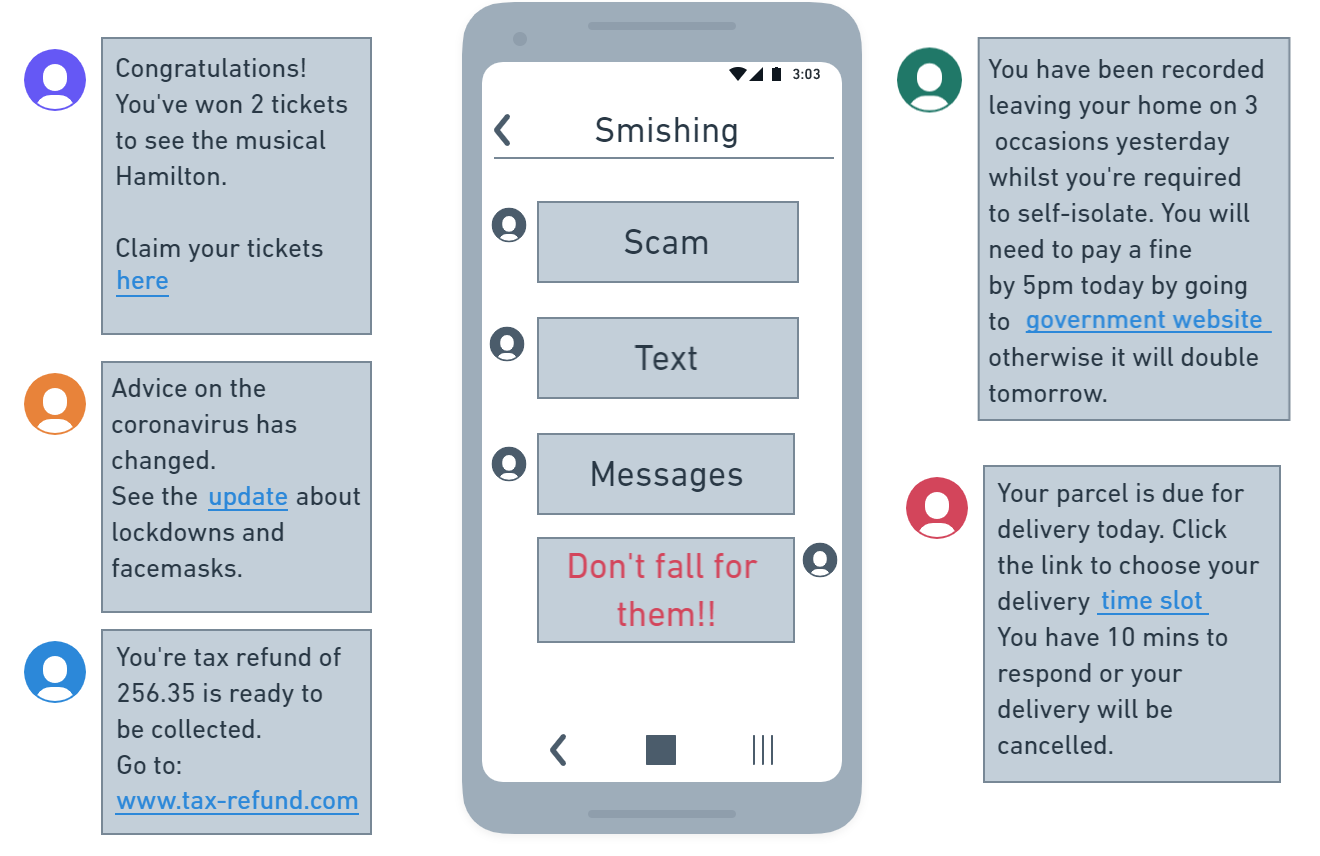
Each of the texts above is a fairly common scam. They all aim to evoke an emotional reaction from you such as 




It’s easy to fall for these scams if you are in a hurry, or if there is a sense of urgency to the message.
The links in these smishing text messages usually lead to a website where they collect the information you enter or download viruses to your device. The consequences of these actions can be very similar to those of vishing attacks.
Sometimes criminals can make a text message look like it came from one of your contacts, which is quite scary and hard to spot. Even scarier is that the text goes straight into any current conversation with that contact on your phone.
It might look something like this:


And it contains a link. At this point alarm bells should start to ring!
In person
Social engineering can occur in person too. Examples include pretending to have been stood up on a date at a restaurant in order to get a free drink or meal, or, more seriously, developing a relationship with someone online and then later asking them for money.

Depending on how well your organisation’s building is locked down, the criminal might be able to get access to restricted sections by following other employees through doors. They might make use of an unlocked laptop at a work station to gain access to files and systems. Or even leave a USB stick containing malware on the desk for someone to pick up and plug in out of curiosity.
Don’t become a victim
- Don’t trust an unexpected phone call or text message. STOP, THINK and DON’T click on links you are not expecting, or give out personal information. Call the organisation’s official business number stated on their website or call your friend to check they sent the link.
- If something sounds too good to be true, then it probably is. Don’t fall for it.
- Make sure you keep up-to-date with the latest scams by following relevant pages on social media, or regularly checking websites such as Action Fraud.
- Never plug in a USB stick that you find; criminals are trying to ‘bait’ you. Always give it to IT to check its contents.
- If you’re ever unsure or suspicious of someone’s identity in an office, politely ask for their ID.

About the author
Laura has recently graduated from Bournemouth University with a degree in Cyber Security Management. During her degree she worked on placement as a Cyber Security Analyst at CybSafe who focus on the people side of cyber security. She is now working as an Information Security Officer at Jisc focusing on information security awareness and communications.
Read more on the GÉANT Cyber Security Month 2020: https://connect.geant.org/csm2020