By Bruno Vuillemin, Security Officer of the University of Fribourg
Sometimes a very simple fraud can cause a great deal of trouble. Whenever you receive and read an email, the sender might not necessarily be the person sending the message! In fact, most smartphones do not display the sender’s “real email address”, but rather what is called the “person’s name” field.
Depending on the software used, this field can be filled in by the users themselves, with no verification at all! An ill-intentioned person can take advantage of this at your expense, with “social engineering” type attacks that not only are very easy to carry out, but are also surprisingly effective.
According to the RFC-5322 standard, a “mailbox” is specified by display name <addr-spec> or by the person’s name <person-s-real@address.com> (e.g.: Brian Smith <Brian@mycompany.com>).
Let’s say you work for “MyCompany” where Brian Smith is the director.
If you received a message like the one below, how would you interpret it?
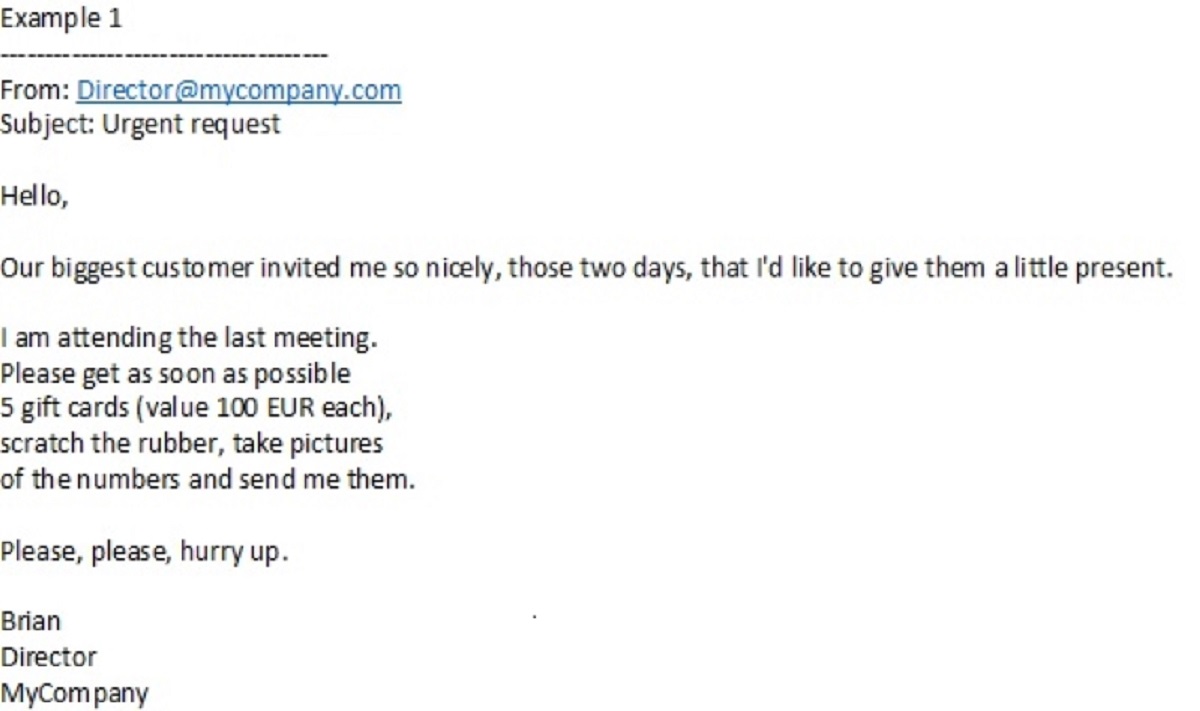
What about a slightly different message, like the one below? How would you interpret it this time?
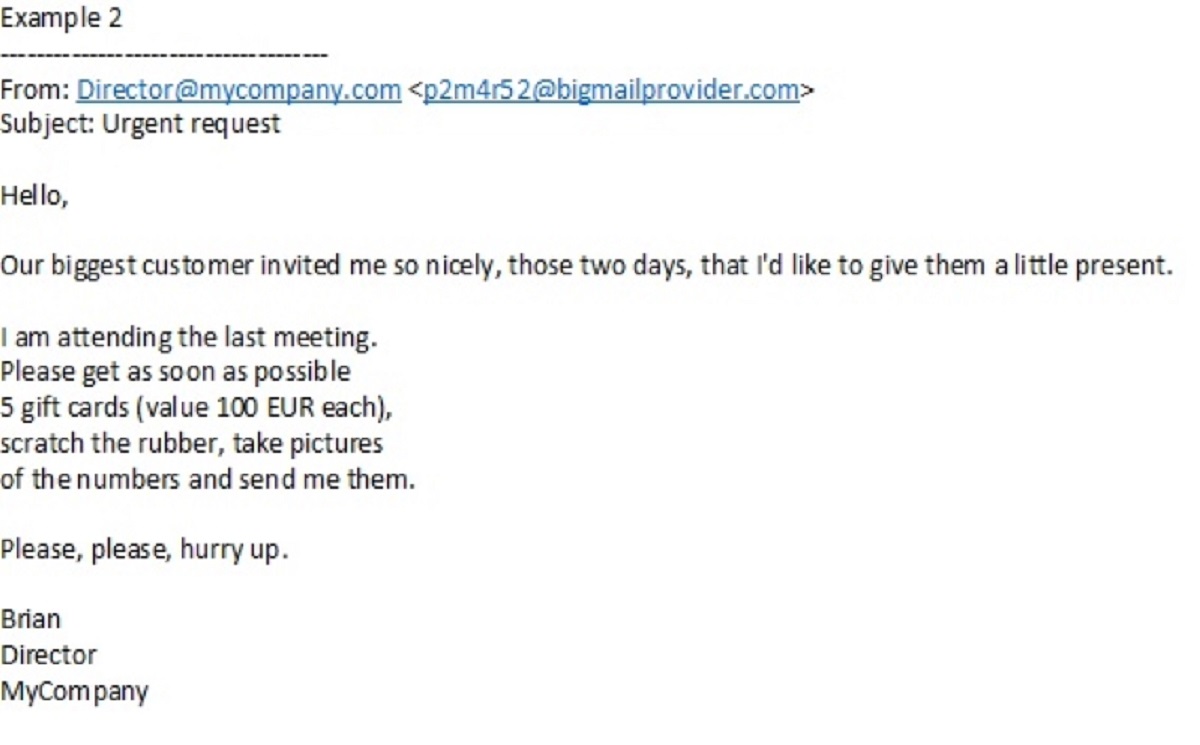
This second example should immediately arouse suspicions regarding the “From:” line!
Too many email clients on smartphones only display the “person’s name” field by default, and more and more email programmes on other platforms (PCs, tablets, webmail) are starting to do the same. Normally, by “clicking” (or simply pressing with the finger on mobile devices) on the sender’s field, the real address (definitely less easy to falsify) finally appears and you can get a clearer idea of the message received. But not many users think about checking this… and get tricked!
Victims of this kind of message will struggle to get their money back. We can also imagine other messages of the same type carrying out social engineering with disastrous consequences for an institution/company and administrative, financial or even penal consequences for the victim.
In conclusion, here is a basic rule: if someone asks us for something unusual by email, we should contact them by different means of communication and ask for identity and message confirmation (for example, by telephone using the official directory of the institution or company).
About the author
First active in the food industry, but already in IT, Bruno Vuillemin joined the University of Fribourg in 1991 where he held various positions (network, SMTP messaging, Unix) before becoming the institution’s Security Officer in 2001.
Read more on the GÉANT Cyber Security Month 2020: https://connect.geant.org/csm2020







