Theoretic training is never as effective as practical training, theoretic knowledge may not always be enough, let’s find out why.
By Justinas Rastenis, VILNIUS TECH
The use of information technology and its importance are growing at the same rate. This is influenced by the extensive use of information technology and the digitisation of data. Unauthorised access to systems or data of interest becomes possible remotely. The only restriction on access to digital information becomes its access and security, not technical or physical capabilities. The problem of information security is also exacerbated by the growing number of potential vulnerabilities. However, even those systems that do not have technical or software vulnerabilities are not resistant to human error or internal attacks. Therefore, an increasing proportion of cyber attacks is the consequence of social engineering.
One of the most common social engineering attacks is phishing. It uses social engineering and technical tricks to deceive or get hold of users’ personal data, banking or other system logins and sensitive user information. Phishing attacks are usually carried out by e-mail. As emails are one of the main forms of data exchange in companies, especially during teleworking, emails for data acquisition have become more prevalent and important. In large email traffic, it can be difficult to distinguish a phishing email from an email from a legitimate user. It is therefore vital to ensure that organisations are prepared to recognise and deal grooming emails.
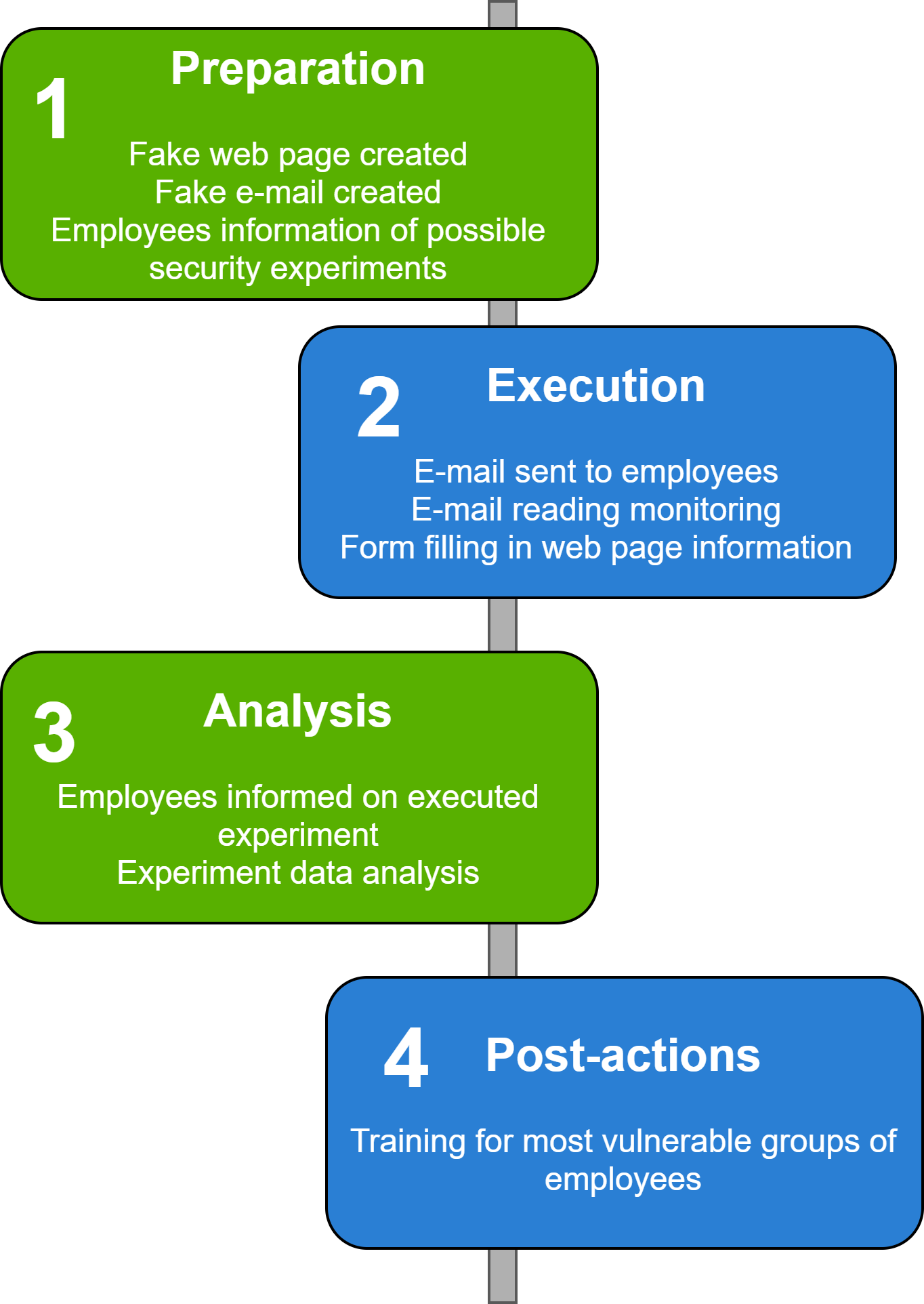
The experiment comprises preparation, execution, data analysis, and post-experiment stages. In the preparation phase, a fake website and email template were created. The theme of the experiment was chosen according to the relevant time of the year – the approaching Christmas period.

As mentioned earlier, the experiment was performed before the Christmas period. 1684 emails were sent on a Friday afternoon and all data was collected by Monday afternoon. During the 72 hours of the experiment or 8 working hours, 708 of the 1648 employees read the letter (43%). Of the 708 employees, 405 downloaded the image and 410 employees opened the website. By performing one or both of these steps, the employee could also download malicious code. Therefore, within 72 hours from receiving the almost 60% of employees who read the email were affected (or 25% of all employees in the organisation) and their actions increased personal and organisational IT security risks. Meanwhile, 214 employees filled out a fake form with their personal data and were completely affected by a simulated phishing attack. That’s 30% of employees who read emails and 13% of all employees in the organisation.

On December 2018 the first experiment, based on the proposed methodology for testing workers resilience data seduction attacks, was conducted. After this experiment, all employees were invited to participate in security training organised by the Information Technology and Systems Centre at Vilnius Gediminas Technical University.
Following this training, there has been an increase in consultations with the Information Technology and Systems Centre on phishing attacks. Each month the centre receives approximately 74 requests to investigate suspicious emails, whilst only a small amount of 19 applications per month were received prior to the training. The growing number of requests to investigate phishing attacks in an organisation can be explained by both the increasing number of phishing attacks and the growing awareness. A second phishing attack experiment was conducted in December 2019. An email with the request to confirm non-deactivation of bank accounts was sent to all employees during this phishing attack. Users were redirected to an external website and asked to confirm or reject bank account disabling, and in another link were asked to fill in an additional form with personal information to avoid future account disabling.
The second experiment, like the first, included the same phases: preparation, execution, data analysis and post-experiment. When repeating this type of extension, it is important not to repeat the same letter and create a different situation. An email sent for experimental purposes should not be obvious and at the same time contain at least a few elements that identify it as a fraudulent e-mail.
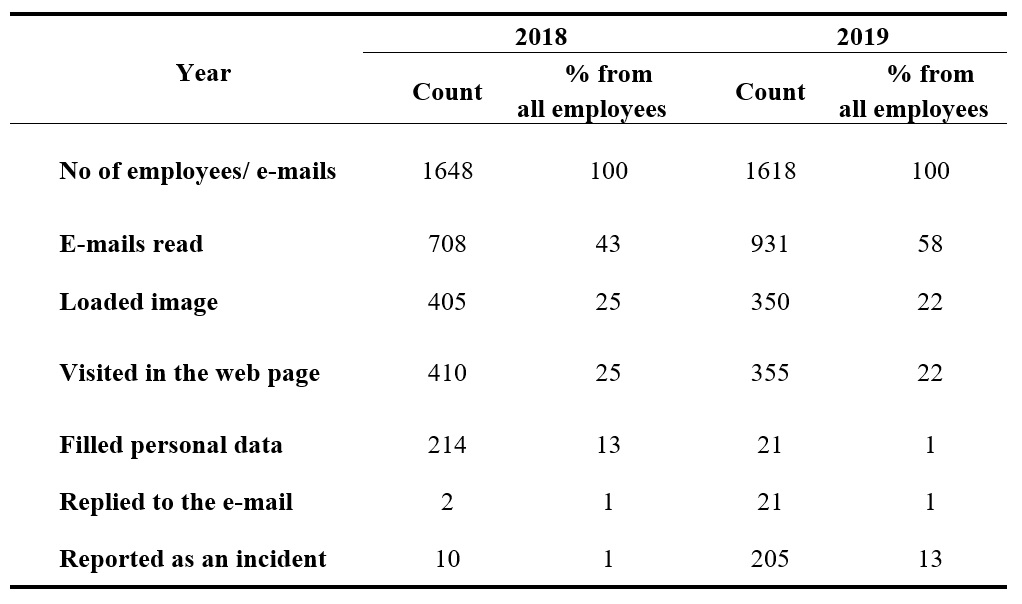
The table above presents a summary of the results of both data seduction experiments. It shows that during the second experiment, employees read the e-mail more actively, but their vulnerability was lower. A smaller proportion of employees downloaded the image, visited the website and filled in the data.
The number of employees who performed all the actions expected by the attacker decreased more than 10 times (from 214 to 21 employees). Meanwhile, the number of reports of a phishing attack rose sharply (from 10 to 205 event reports). These figures are very representative, but 1% of all workers are still vulnerable. The number of vulnerable users is still too high and needs to be reduced in the future.
Security training shows positive results in companies and organisations. Even organisations like NIST (National Institute of Standards and Technology) provide information and training programmes on security. However, the results of security training can vary as different training methods and formats can be applied, in addition, different groups of learners have their own preferences, hence, it’s important to tailor security training to a specific audience and topic.
I definitely recommend organisation check-ups to increase employees and students’ vigilance against cyber attacks. The lack of employee education and awareness programmes will make organisations increasingly vulnerable to cybercrime.
Author
I’m Justinas Rastenis from Vilnius, Lithuania. In 2010 I graduated in Informatics at Vilnius Gediminas Technical University (VILNIUS TECH), in 2012 I obtained my master degree in engineering informatics at VILNIUS TECH. Since 2007 I have been working in Information Technology and system centres at VILNIUS TECH, in 2012 I became lecturer in the Information systems department. I’m interested in Information Technology, cyber security and in the deployment of new infrastructure services.
Also this year GÉANT joins the European Cyber Security Month, with the 'Cyber Hero @ Home' campaign. Read articles from cyber security experts within our community and download resources from our awareness package on https://connect.geant.org/csm2021








