By Tommaso Rescio, Francesca Soro, Giulia Milan – Centro SmartData@PoliTO – Politecnico di Torino
The measures adopted to reduce the spread of the Covid-19 pandemic have undoubtedly changed not only our way of life, but also our way of working. For example, for many jobs, the only solution to ensure at the same time social distancing and operational continuity is working from home. This solution, however, comes with a major drawback: it exposes users to new types of attacks, due to the tools chosen to collaborate with colleagues and to share/access resources from home.
Attackers are exploiting vulnerabilities on these types of tools. Rapporto Clusit 2021 reports a global increase in cyber attacks of around 12% in 2020 compared to the previous year. Around 10% of the attacks in 2020 can be related to new threats linked to the Covid-19 pandemic.
Cyber criminals have targeted in particular employees who log into remote computers on unsecured networks. Access to such computers is based on the Remote Desktop Protocol (RDP) on Windows systems, or Secure Shell (SSH) which allows anyone to connect and access the computer after a login phase. Unsurprisingly, connection attempts to RDP/SSH servers have seen major increases during the pandemic, with attackers trying to login into the computer using brute-force attacks. How? In a nutshell, attackers use huge lists of usernames and passwords to gain access to an account and, with the rise of working computers online, the number of login attempts exploded. For instance, ESET telemetry recorded a staggering 768% increase in RDP attacks between Q1 and Q4 2020.
How many attacks does your PC see? Which passwords do attackers use?
Here at Politecnico di Torino, we have built a smart monitoring system to observe and study cyber attacks and develop strategies and methodologies to be protected. We created some fake PCs that we are using to deceive attackers: hackers believe they are attacking real computers, while we observe and study them and their behaviour. Here are some key facts:
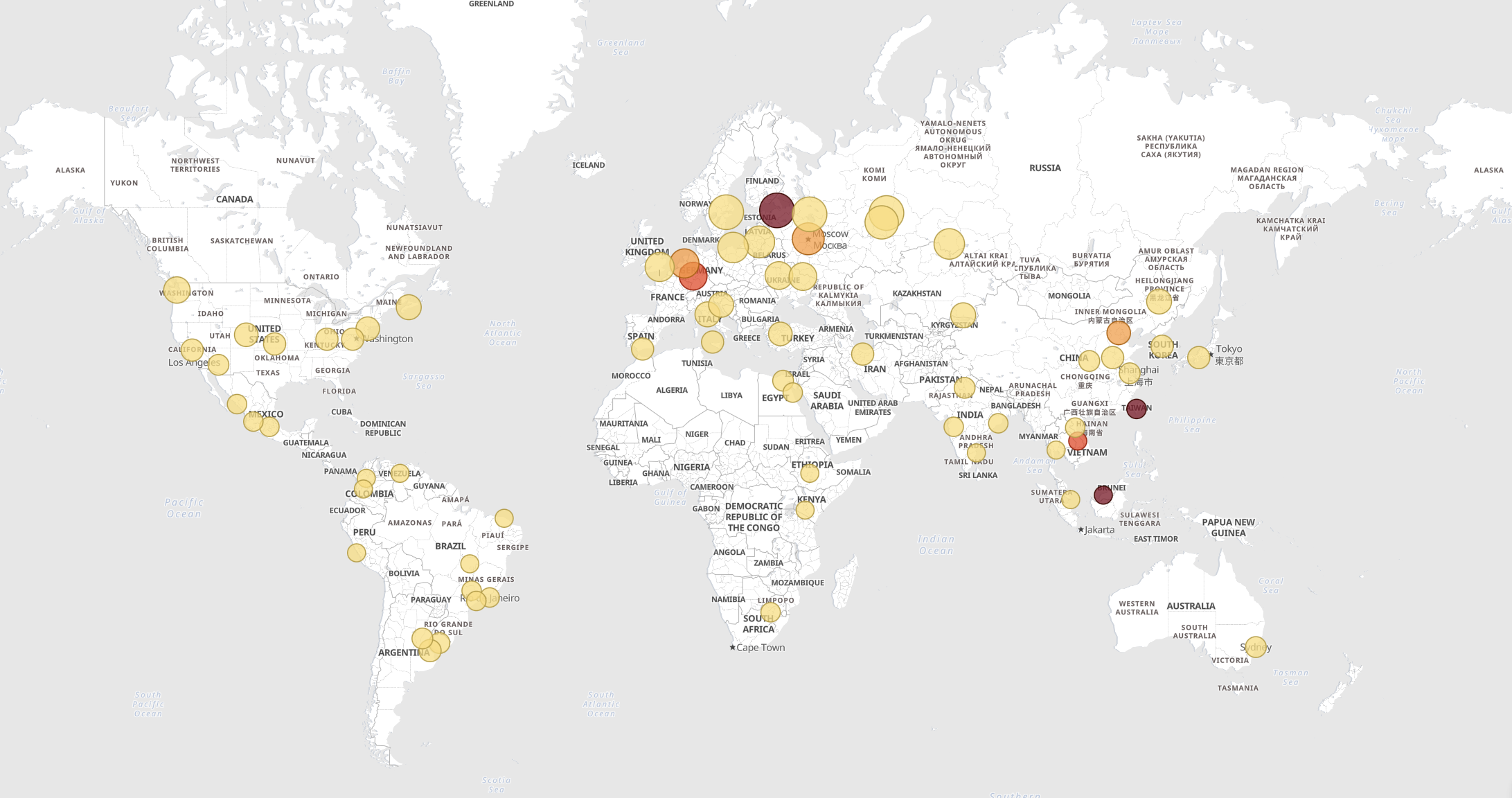
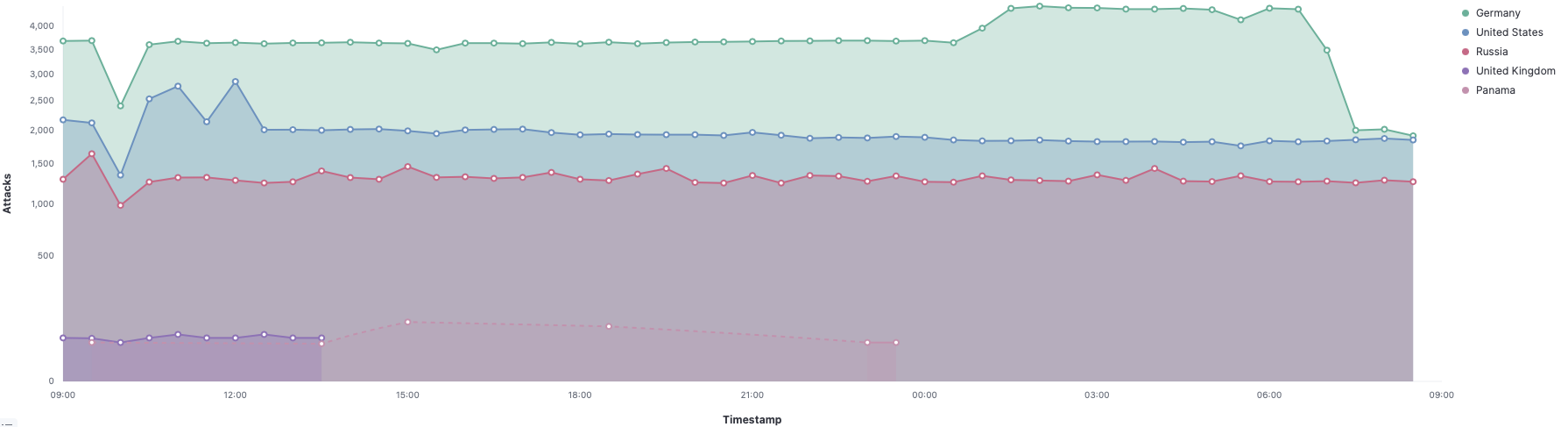
Fig. 1 shows a map with the locations of attackers, while Fig. 2 instead shows the number of attacks received over time from some countries: we observe that most of the attacks come from Germany, Russia, United Kingdom, USA, etc. Attacks come at a constant rate overtime, with on average 10000 attacks per hour! Each of these attacks corresponds to a login attempt, where the attacker tries to gain access to your computer.


Thanks to our infrastructure, we have also recorded the most used usernames and passwords tested by the attackers. Fig. 3. shows the results. The most common user names are root and admin while the most common passwords are admin and password. There are a lot more complex combinations that attackers try to use.
What can you do?
To prevent these attacks, you should choose a so-called strong password: the longer the better is a rule of thumb. The password should not contain references relating to easily traceable private or professional life, it should not contain a consecutive series of only numbers or only letters, indeed mixing letters, numbers and special characters strengthens the password. You should use a different password for every digital service and consider enabling 2 factor authentication for important services.
While using a strong password is a must, what is even more efficient is to avoid exposing your PC to the internet. Configure the firewall to block RDP and SSH services so that only authorised IP addresses can access those services. Even better, if you need to access a remote computer, consider to configure and activate a VPN to connect to the corporate network, and then access the remote computer from there. A side note: moving the service from the default port to a different port does not work. We see attackers who try to abuse RDP/SSH services on practically any port. So be warned!
About the author
Tommaso Rescio
Tommaso Rescio is a Research Fellow at Politecnico di Torino. He received his Bachelor’s degree in Computer Engineering at Università Degli Studi di Firenze in 2018. He received his Master’s degree in Communications and Computer Networks Engineering at Politecnico di Torino in 2021. In 2021, he joined SmartData@Polito as a GARR Research Fellow. With his master thesis he won a Consortium GARR scholarship. His research interests focus on traffic monitoring for cybersecurity.
Also this year GÉANT joins the European Cyber Security Month, with the 'Cyber Hero @ Home' campaign. Read articles from cyber security experts within our community and download resources from our awareness package on https://connect.geant.org/csm2021







