By Nicla Ivana Diomede, Chief Information Security Officer at the University of Milan
What is Phishing?
Phishing is a type of fraud aimed at illegally stealing confidential information such as login credentials (username and password), credit card numbers and so on. Email is the main attack vector, but text messages, chat and social media can also be used. In general, the fake sender presents himself/herself as an authoritative subject (e.g. bank, Administration, IT Service Managers, Directors) and asks the potential victim to urgently carry out some activities in order to avoid blocking a service or to take advantage of a promotional offer.
Phishers use the data obtained to carry out the fraud: for example, using the username and password obtained (identity theft) they carry out illegal activities, or make purchases at the expense of the victim or banking transactions.
Phishing attacks are becoming so sophisticated, growing more and more and often use social engineering techniques. They aim to carry out financial crimes, cyber espionage and information influence operations.
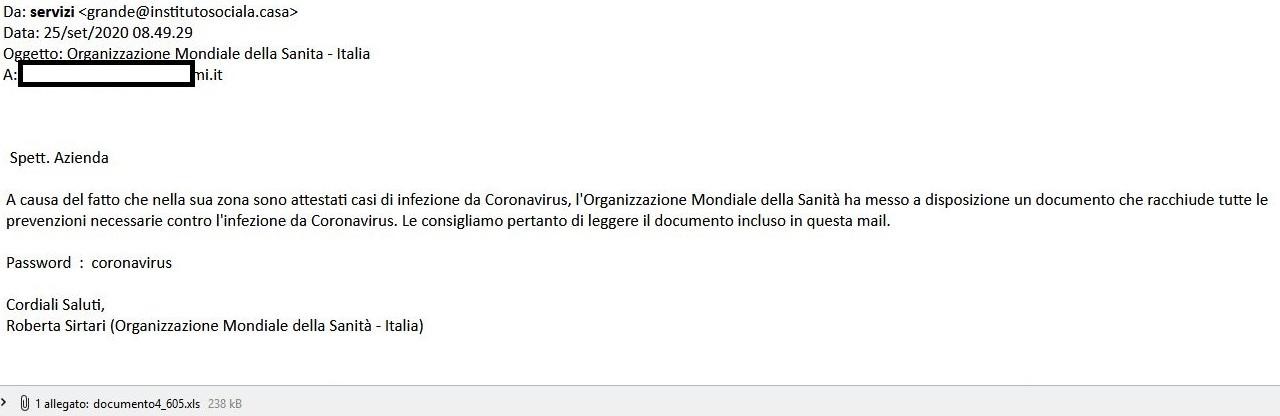
Phishing during the COVID emergency
During the COVID emergency world-wide, there has been an intensification of both malicious email campaigns and the proliferation of new malevolent domains and websites on COVID.
Experimental data shows that during the Corona virus emergency not only phishing and social engineering campaigns increased but also the number of potential victims contacted on Institutional email accounts and consequently also the number of violated user credentials grew exponentially.
The explosion of phishing campaigns, focused on COVID, aims to exploit two conditions:
- General fear, the sense of urgency and solidarity related to the Health Emergency
- The remote use of personal PCs from home by workers during lockdown. Phishers take advantage of the lack of secure protection available at infrastructural level on corporate systems within the company network.
The goal of malicious email campaigns related to COVID is mainly to violate user account credentials or spread malware in order to compromise devices, data and try to establish an access point to the company network.
Cultural and organisational measures to defeat phishing
At the organisational level, policies about behaviour for the secure management of IT tools must be adopted and known by all users with the goal to prevent phishing. Users need to know what to do if they receive suspicious emails, what to check in order to recognise them and the procedure to promptly report suspicious emails to the Security Team.
It is important to provide security training and awareness programmes with phishing email simulations for all users in order to be ready and responsive.
Furthermore, policies about behaviour must also be adopted in order to always check the identity of those submitting requests (including phone calls) and to reduce social engineering attempts.
At the organisational level, the procedure of managing phishing attacks must be defined and designed, together with inputs, constraints, outputs through repeatable and replicable workflows. This way the Security team will deal with phishing attacks efficiently, promptly, effectively by limiting their effects and immediately managing compromised systems or accounts.
Technological measures to defeat phishing
- Adoption of a SOAR solution (Security Orchestration Automation and Response) with specific playbooks to defeat phishing. Due to a continuous and constant growth of dangerous threats, the adoption of SOAR platforms with “phishing playbooks” allows to simplify the incident management process. It allows to automate repetitive or time-consuming tasks that can be executed at machine speed, to identify false positives and improve accuracy, to reduce the risk of human error, to interact automatically with other security platforms, so as to improve efficiency when responding to known threats and to allow the Security team to focus on the most strategic tasks or the most insidious threats.
- Adoption of Multi Factor Authentication (MFA) and blocking of other forms of legacy authentication from outside the company area. The MFA overcomes the problem of password re-used by users or not secure and strong passwords.
- The widespread use of the company VPN to all PCs, including the private ones of remote workers, in order to apply the security controls used on the company network.
- Implement network segmentation and keep home devices segregated because they are usually not fully patched.
- Adoption of application firewalling systems (or of proxy) in order to automatically detect and block navigation to dangerous websites known as phishing, malware, hacking, unclassified.
- Make sure that all PCs, even private ones, are equipped with endpoint protection solutions (EDR if it’s possible).
- Automatic blocking of macro execution in Office documents attached to emails or downloaded from outside of the organisation’s network.
- Anti-spoofing checks: implementation on email servers of anti-spoofing checks (SPF¹, DKIM², DMARC³) with hard fail and reject criteria where applicable, in order to verify if the content in an email is secure or malicious. This improves the efficiency of the standard filters adopted by blacklist-based spam services. However, these tools are not enough to fully protect against emails with a forged From field.
- Adoption of antispam and Antivirus solutions on email servers, able to analyse and block malicious attachments or attachments with particular extensions and check the URLs within the body of the emails.
- Automatic notification systems via email to inform users about emails from external domains with the disclaimer of the rules for the secure email management.
- Automatic scanning and sandboxing of files from external domain
- Adoption of password strength policies and implementation of automatic mechanisms to prevent the use of weak passwords.
- Enabling and sending of mail server logs to SIEM (Security information and event management) equipped with specific rules.
Footnotes
¹ Sender Policy Framework (SPF) is a protocol that allows you to check if an email has been sent from a server authorized to send emails for the sender’s domain (Envelope-From field). The list of hosts authorized to send emails is published via DNS in the form of TXT records. In fact, by examining the header of an email it is possible to check which domain the email actually comes from.
²DomainKeys Identified Mail (DKIM) is a protocol for signing some parts of the email in a digital way, in order to ensure that they have been sent from the protected domain (From field) and that they have not been altered. The list of public keys to check an email is published via DNS as TXT records.
³Domain-based Message Authentication, Reporting & Conformance (DMARC) is a protocol that, together with DKIM and SPF, allows you to specify how to check the emails of a specific domain and to define report mechanisms for the protected domain in case of counterfeit emails. It allows you to constraint the alignment of the From field with the Envelope-From field.

Nicla Diomede is the CISO (Chief Information Security Officer) at University of Milan (UniMi), coordinating and leading the University structure, responsible of “Cybersecurity, Data Protection and Compliance”. She is member of “Cybersecurity and Personal Data Protection Committee” and member of the control room on ICT Strategies at UniMi.
Since the 2000s she has interested in emerging cybersecurity topics, contributing significantly to the organization of the CSIRT and SOC at Milan University, one of the first in the national academic world.
LinkedIn
Twitter: @NiclaDiomede
Read more on the GÉANT Cyber Security Month 2020: https://connect.geant.org/csm2020







