By Michele Scalas, Davide Maiorca and Giorgio Giacinto, University of Cagliari
Ransomware represents a serious threat that acts by locking the compromised device and encrypting its data (along with exfiltrating private information), forcing the device owner to pay a ransom to restore the device functionality or to avoid that the stolen data is publicly available. Attackers typically develop such dangerous apps so that normally legitimate functionalities (e.g. encryption) perform malicious behaviour; thus, making them harder to distinguish from genuine applications.
This kind of threat also affects the mobile domain, including the Android platform. In the following, we illustrate how such attacks towards Android work and the recent research efforts to uncover them.
Attack strategies
Typically, two methods are used to perform Android ransomware attacks: locking and encryption. In the first case, attackers take the following strategy:
- They create visible, overlay screens (i.e. windows put on top of any other screen) that cannot be dismissed by the user;
- They force such screens to stay always visible, even when they get killed or the device is rebooted;
- They disable the navigation buttons, such as the back
Such created screens — as in Figure 1, where the ransomware app acts as a law enforcement agency — include a threatening message that instructs the user to perform the ransom payment, which will (theoretically) permit to suppress the permanent screen.
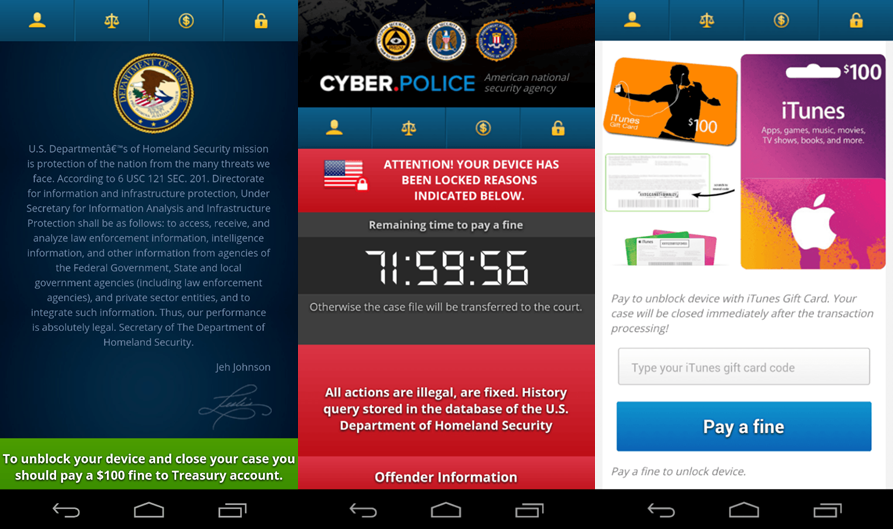
Newer versions of Android have implemented countermeasures as a response to this strategy. For example,
- the device can be booted in Safe Mode, where the system blocks third-party apps from running
- starting overlay screens is not possible without showing a notification
- the status bar takes priority and shows a specific notification that allows disabling overlay screens.
However, these recent Android versions do not reach the majority of devices as of September 2020. Thus, locking behaviour remains a relevant threat.
In the case of crypto-ransomware apps, the attacker shows a window that could not necessarily be constantly displayed, because his/her main focus is to perform encryption of the user data (e.g. photos, videos, documents). Therefore, paying the ransomware is needed to decipher the data.
A notable characteristic of this scheme is that it consists of malicious usage of legitimate system functionalities and components. For example, showing a non-dismissable screen is often used to avoid accidental touches by users that may cause them to miss the screen’s content. Equally, encryption is not malicious in itself, since it is usually employed to store sensitive data generated by the apps securely. This fact makes ransomware incredibly deceitful; thus, the challenge for security experts is to carefully point out the traits that distinguish malicious behaviour from legitimate behaviour.
How AI can detect and explain ransomware
Artificial intelligence — Machine learning, in particular — has been increasingly used to develop Android malware detection systems, i.e. tools that classify an app as malicious or legitimate. In our studies, we have shown that ransomware can be detected through machine learning algorithms by training them to analyse a small set of characteristics (the so-called features of the algorithm) in the structure of the apps. We have studied the practical feasibility of our approach, evaluating its resilience and the computational cost on a mobile device.
More recently, we’ve been proposing methods to discover the specific traits that characterise Android ransomware attacks. To do so, we employ explainability techniques, which are experimental tools that allow understanding the knowledge learned by machine learning models. This way, the research community aims to identify the most preeminent features characterising ransomware apps, at the same time pointing out the weaknesses of current AI-based detectors.
As an example, in one of our exercises, we have considered a basic set up where we make use of two types of features: i) the calls to system functionalities and ii) the request of permissions. The rationale behind this choice in the following:
- Calls to system functionalities: locking and encryption actions require the use of elements that involve core functionalities of the system, e.g. to keep windows constantly displayed or execute encryption routines. As an attacker, coding new libraries to perform these kinds of actions would be extremely inefficient. Therefore, it is preferable to rely on functions already included in the Android system. For example, we expect the usage of system functionalities that lock the screen or reset the lock-screen password. For crypto ransomware, it is likely to make use of standard functionalities for managing files or performing file encryption;
- Permission requests: The Android operating system requires the app developer to request permissions to use a particular functionality. Depending on its dangerousness, one permission can be granted automatically or after an explicit user agreement. Consequently, we expect that common permissions (e.g. INTERNET to let the app connect to the Internet) will be associated with trusted apps, while dangerous ones (such as WRITE_EXTERNAL_STORAGE to let the app write into the device storage) could be typical of ransomware samples.
New research directions
Through our work, we identify and explain the main traits of Android ransomware, highlighting the characteristics of each family and the attacks’ evolution over time in terms of application components. As shown in Figure 2, the extracted explanations reveal that each feature — a system call or permission (in capital letters) — indicates ransomware behaviour (positive values) or legitimate one (negative values) depending on the characteristics of the considered ransomware family or period of creation. In fact, attackers constantly develop new stratagems to fool malware detectors.
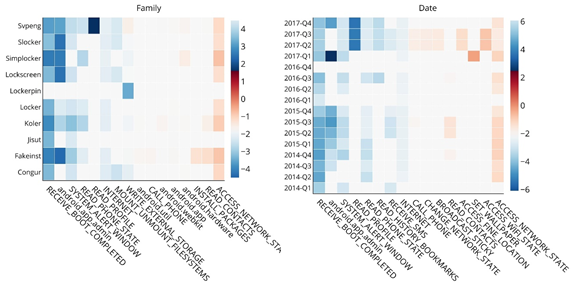
Our analysis has corroborated previous evidence that system calls and permissions effectively catch the peculiar actions operated by ransomware apps. The proposed approach can then be used to test the effectiveness of other features. Ultimately, it lies in a new research direction tailored to improve malware detectors’ design process, where explanations can help experts to characterise attacks effectively and, eventually, perform more accurate detection.
References
- Cara, M. Scalas, G. Giacinto, and D. Maiorca, “On the Feasibility of Adversarial Sample Creation Using the Android System API,” Information 2020, Vol. 11, Page 433, vol. 11, no. 9, p. 433, Sep. 2020.
- Scalas, D. Maiorca, F. Mercaldo, C. A. Visaggio, F. Martinelli, and G. Giacinto, “On the effectiveness of system API-related information for Android ransomware detection,” Computers & Security, vol. 86, pp. 168–182, Sep. 2019.
- Melis, D. Maiorca, B. Biggio, G. Giacinto, and F. Roli, “Explaining Black-box Android Malware Detection,” in 2018 26th European Signal Processing Conference (EUSIPCO), 2018, pp. 524–528.
- Sophos, “The State of Ransomware 2020”, Survey on 5000 IT Managers, May 2020. (last accessed October 2020)
About the authors
Michele Scalas has a M.Sc. degree in Telecommunications Engineering from the University of Cagliari. He is now a Ph.D. student at the Pattern Recognition and Applications Lab of the University of Cagliari. His research interests include malware detection and explainable machine learning.
Davide Maiorca received a M.Sc. degree (Hons.) in Electronic Engineering and a Ph.D. in Computer and Electronic Engineering from the University of Cagliari (Italy). He is currently Assistant Professor at the Department of Electrical and Electronic Engineering, University of Cagliari. His current research interests include adversarial machine learning, malware in documents and Flash applications, Android malware and mobile fingerprinting.

Read more on the GÉANT Cyber Security Month 2020: https://connect.geant.org/csm2020









