By Francesco Ficarola, Università La Sapienza, Rome
Warning: picture ahead showing animal in distress
If you are reading this, then chances are that you have heard of Social Engineering (SE) at least once in your life. Perhaps, right now, you are thinking “how do I influence my boss to get a raise?”. Yes, don’t worry, I won’t tell him about your plans. Many of us are not satisfied with our salaries. So, that could be a good reason to “hack” a person, right? Seriously, you shouldn’t, just ask for that and cross your fingers.
However, even if we ask for a pay rise by simply sending an email to our boss with good intentions, we unconsciously try to persuade him. We promote our work and highlight the goals we achieved. We list all the good things we have done for the company in order to manipulate his/her perception. We prefer not to recall our mistakes because those could cause bad thoughts. So… congratulations, you are already adopting some basic rules of SE!
Social Engineering is everywhere
SE didn’t originate in conjunction with the birth of Personal Computers or during the internet era. SE was born when humans started interacting physically. In 1983 Robert Cialdini wrote one of his best books: “Influence: the Psychology of Persuasion”. Cialdini is considered the father of persuasion techniques and social engineers use such techniques to hack other humans. And guess what? You can use SE everywhere, with anyone; you just need to be persuasive. Yeah, I know you were the little bad boy who called your grandmother pretending to be an electrician. You altered your voice, you told her about an imminent electrical fault, then you turned the power off.
How do Social Engineers act?
However, innocent jokes aside, there was one person who made SE famous during the early years of the computer age: Mr. Kevin Mitnick (aka “The Condor”). Mitnick was one of the first hackers using SE techniques to hack IT systems after getting useful information from IT administrators or technicians. He could present himself as someone else and ask for private information, such as credentials. He understood the weakest link in a chain is human. Thanks to his ability of impersonating someone else, he managed to hack into computers, companies and telecommunication infrastructures.
This kind of technique is nowadays called pretexting and is one of the fundamental methods used by social engineers. One of the main objectives of the pretexting technique is to gain trust from the victim. If you can trust someone, then you are more inclined to talk about yourself and do what is asked of you. If I’m able to be pleasant to you and make some kind of connection between us, then you will trust me more.
Perhaps you have already received an email in which the sender pretended to be someone or something else. One of your friends or your bank? Well, such emails are very frequent and along with “impersonation” they are part of a SE attack. So, the practice of sending “fake” emails with the goal of influencing or gaining personal information from the victim is called phishing. Ok, you already know that, but did you also know about the existence of vishing? This term is not famous as much as phishing, but this attack, accomplished through a voice call (yes, the “v” stands for voice), is designed to get you to share personal information. Similarly, smishing uses mobile phone text messages (SMS) for the same purposes.
According to “2020 Verizon Data Breach Investigations Report”, phishing is the first threat action in breaches (Fig. 1) and the second attack vector utilised by cyber criminals (Fig. 2). So, you can well understand that SE techniques are emerging more and more as hacking tools.
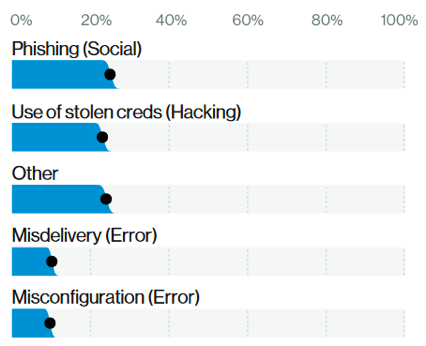
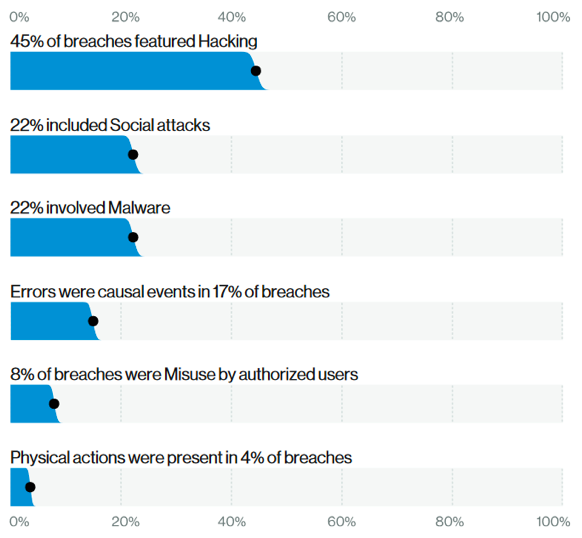
Of course, a SE attack through a phishing email or a phone scam is not carried out without first obtaining some information about the victim. For that reason, social engineers first search and gather data about you, then they usually collect all the information in a sort of dossier. This practice is known as doxing and helps social engineers to create a perfect pretext. They know you are a doctor, with two children and love dogs. They also know you adopted a street dog because you published its photos on Facebook. So, it’s not difficult to imagine what kind of pretext they may use. Let me show you an example.

How do you feel right now? Pretty bad? I know, that’s very cruel and unfair. No dog should go hungry like that. I love all animals and I really feel bad as I see one of them suffering. I suppose this kind of emotion is shared by many of you. And this is the point!
Social engineers know that such images can arouse intense emotions. Their aim is not to make you think. If you think too much, then you can understand they are deceiving you. On the other hand, if you are overwhelmed by emotions, you will surely act on impulse. Thus, they could ask you to help this dog by sending a certain amount of money to a (fake) animal rescue organisation. Or, maybe, they could ask you to share an Instagram post by clicking on a certain (malicious) link.
How can we prevent SE attacks?
It’s not always easy to understand if we are victims of a SE attack. However, I’d like to conclude this article by reporting the three fundamental rules you must follow in order to reduce the risk.
- Never click or visit web pages you may receive through an email or a phone text message if you are not 100% sure about the sender. Thus, always check its email address as well as its name. Read and spell every character of its address. Anything weird like anazon.com instead of amazon.com? Delete that email!
- Do not provide your personal information. Remember, your bank will never ask for your PIN or credit card number. Similarly, your company IT administrators can’t ask for your credentials to solve a “ghost” issue.
- Do not download, open files attached to an email you do not expect to receive. If it seems that the email was sent by one of your friends, first contact him/her through a different communication channel, such as instant messaging, and ask if he/she really sent that email.

Francesco Ficarola received a Degree, a Master and a Ph.D. in Computer Engineering from Sapienza University, Rome where he now works as a Cyber Security Officer.
Linkedin
Twitter: @f_ficarola
About the Sapienza University of Rome
With over 700 years of history, 114000 students, 4000 teachers and 3000 employees, technicians and librarians, in addition to 2000 administrative staff in university hospitals, Sapienza is the first university in Europe. Its mission is to contribute to the development of a knowledge society through research, excellence, quality education and international cooperation. Thanks to a wide network of agreements with universities around the world, Sapienza also provides its students many international opportunities, including double degrees, scholarships abroad, internships in European and non-European countries, and international PhDs.
Read more on the GÉANT Cyber Security Month 2020: https://connect.geant.org/csm2020







